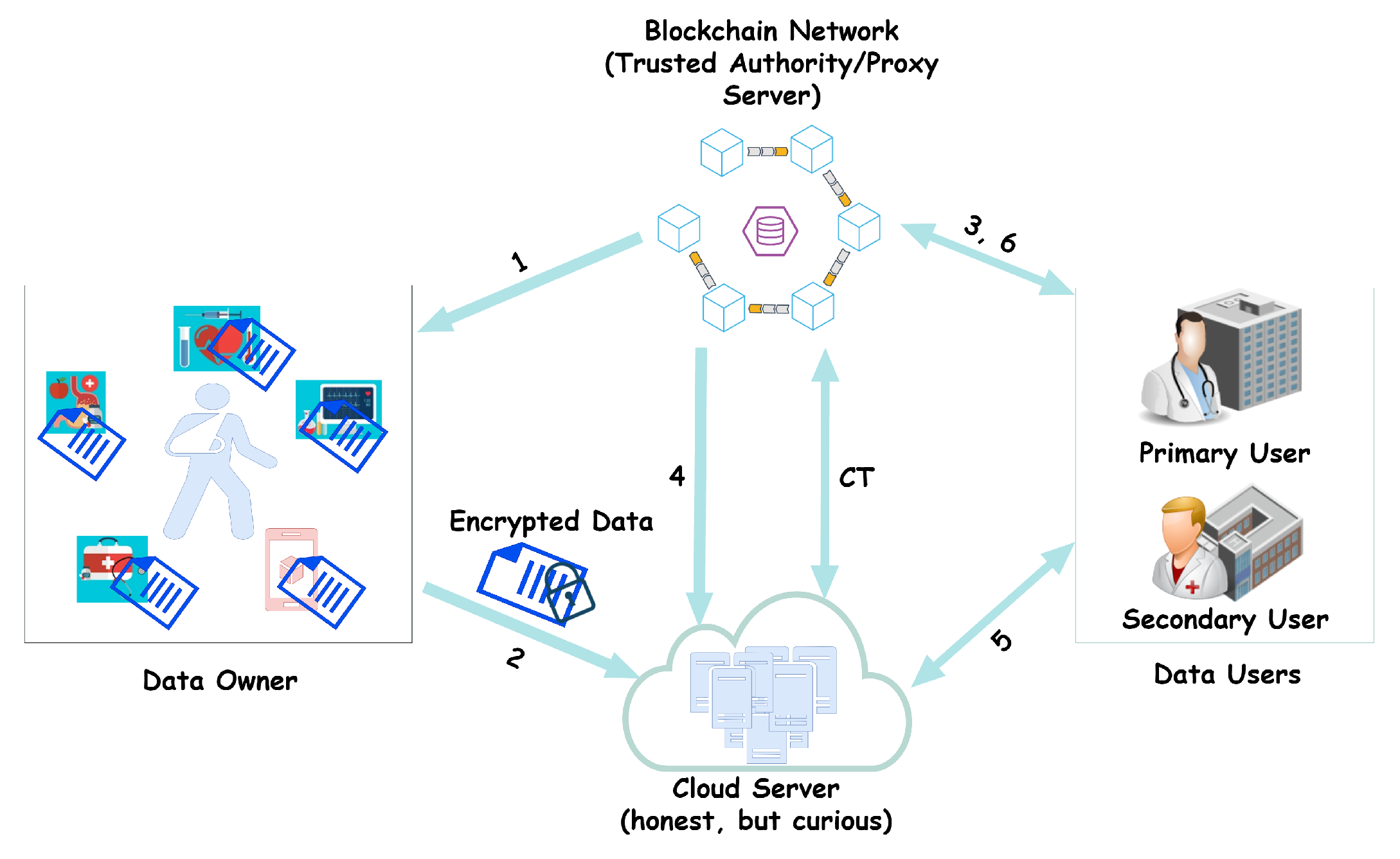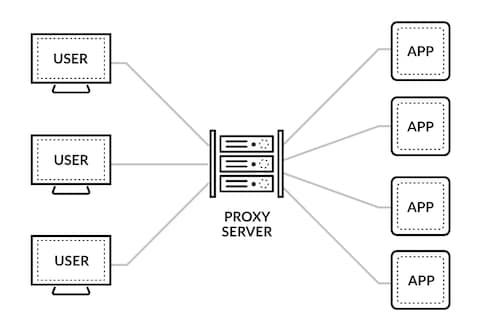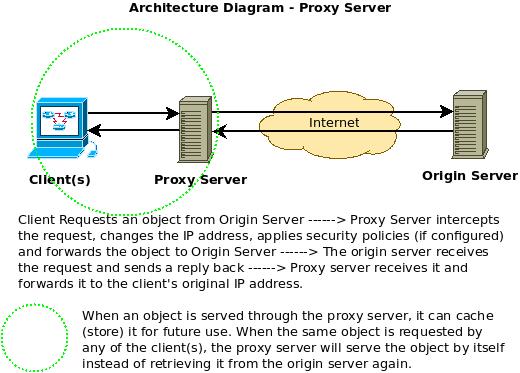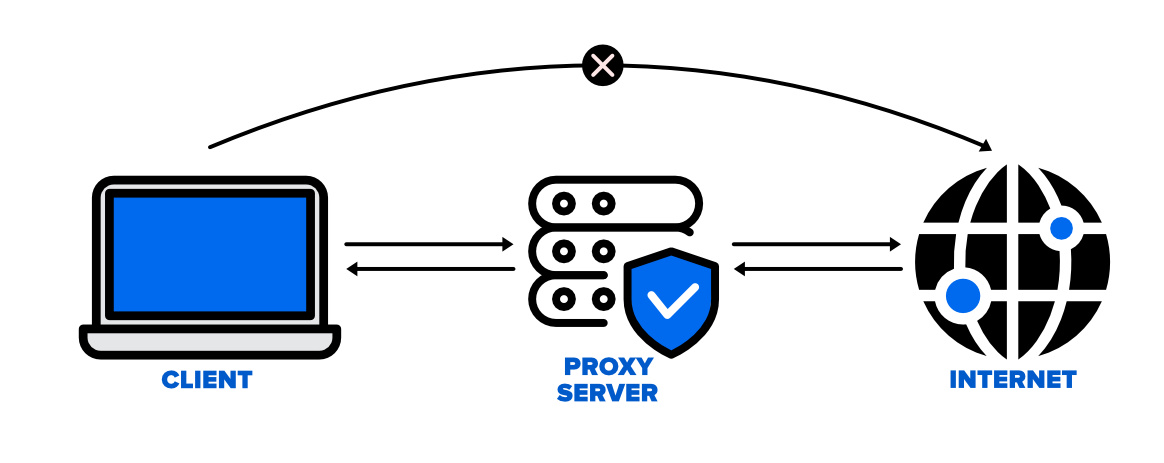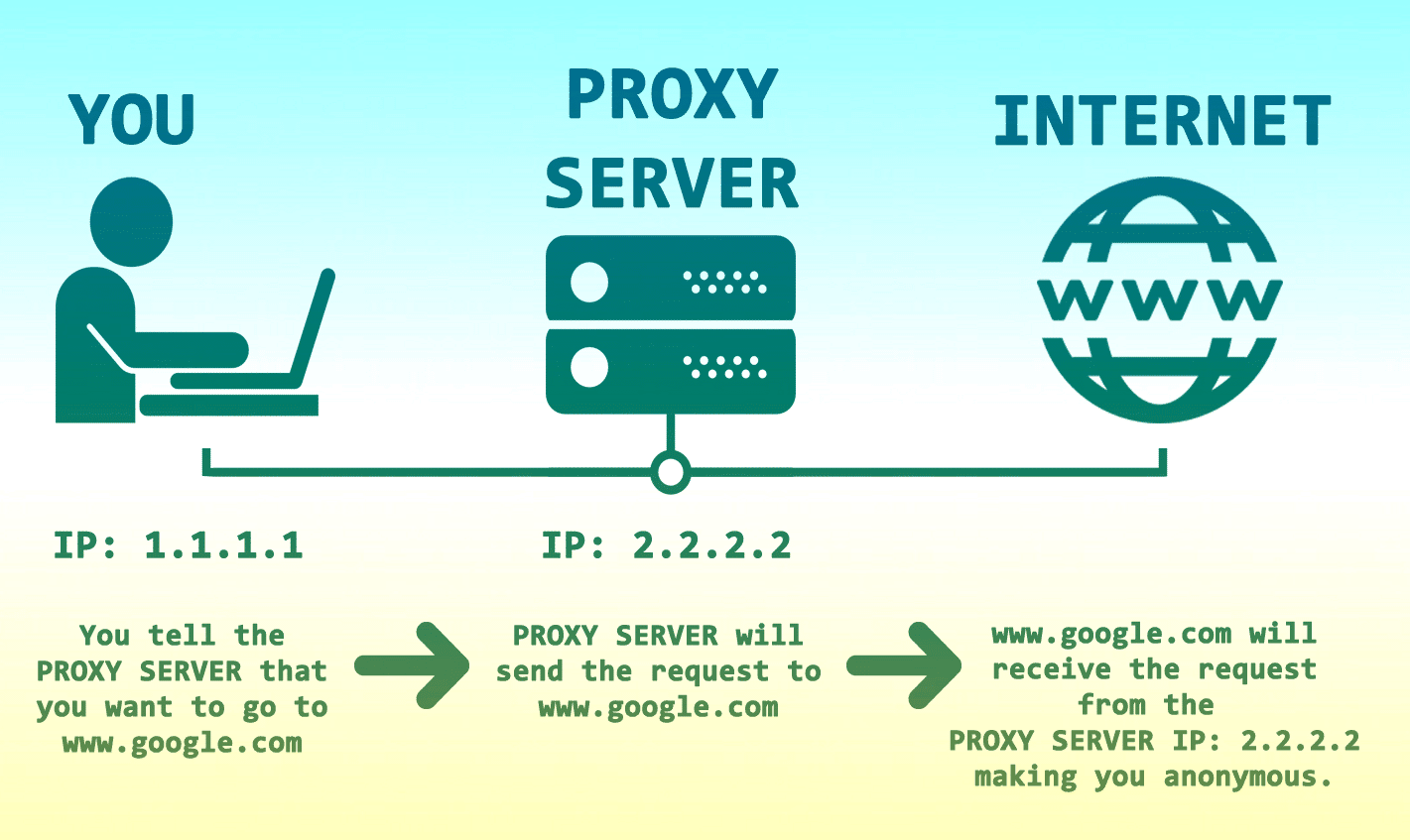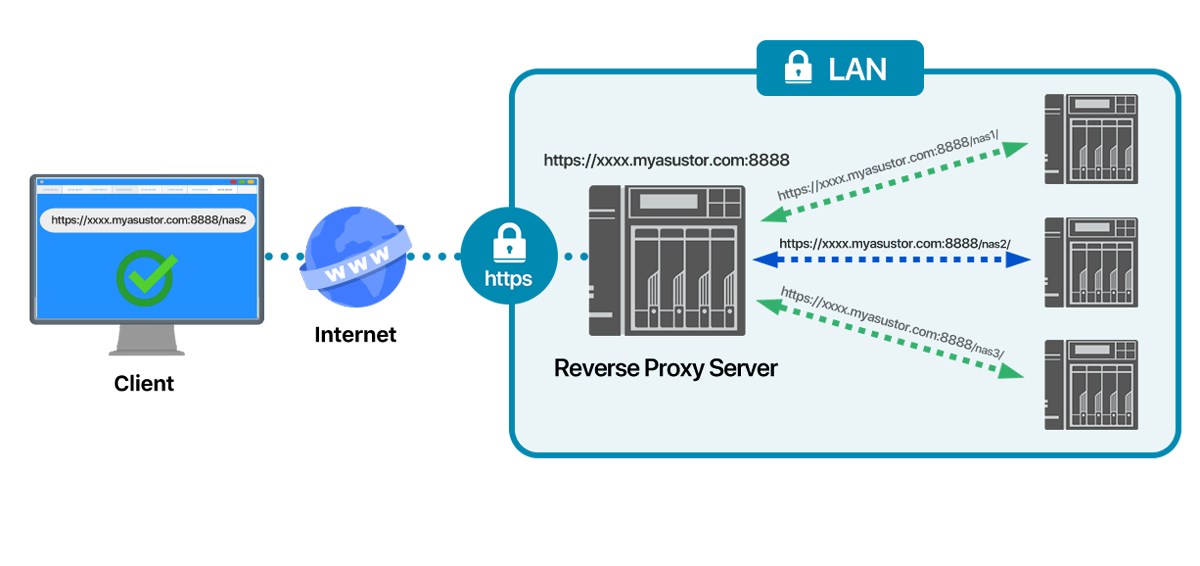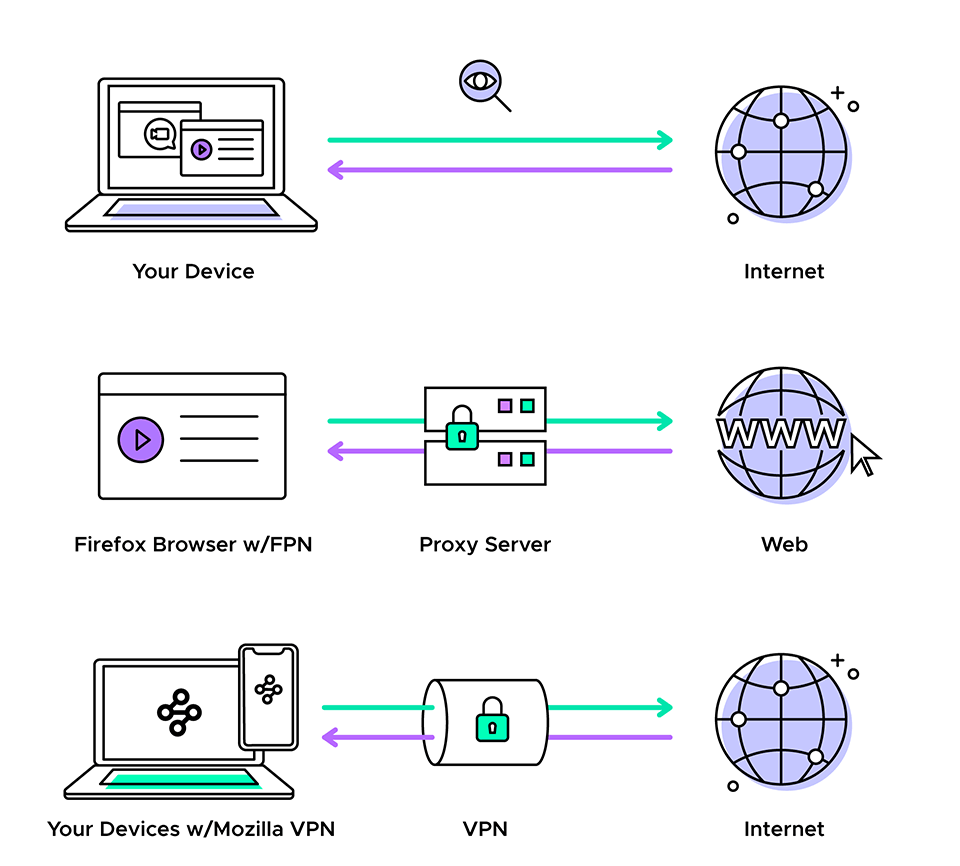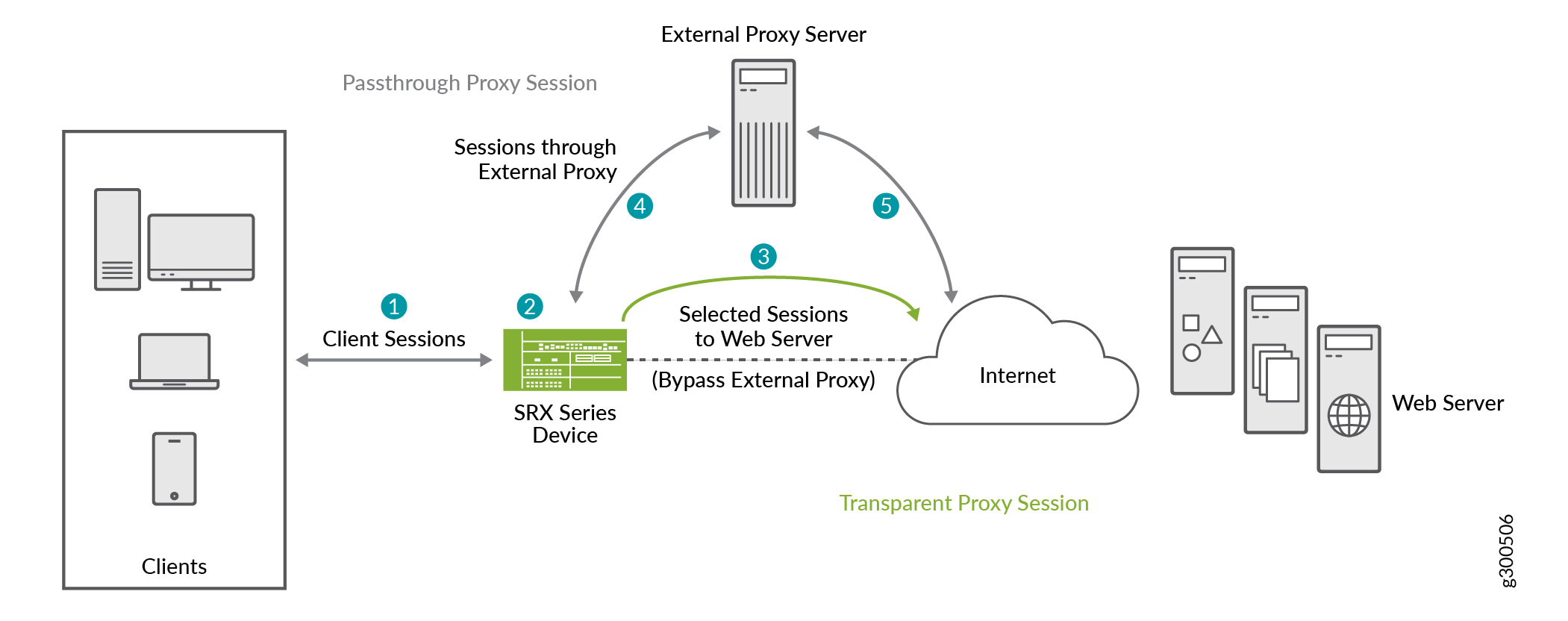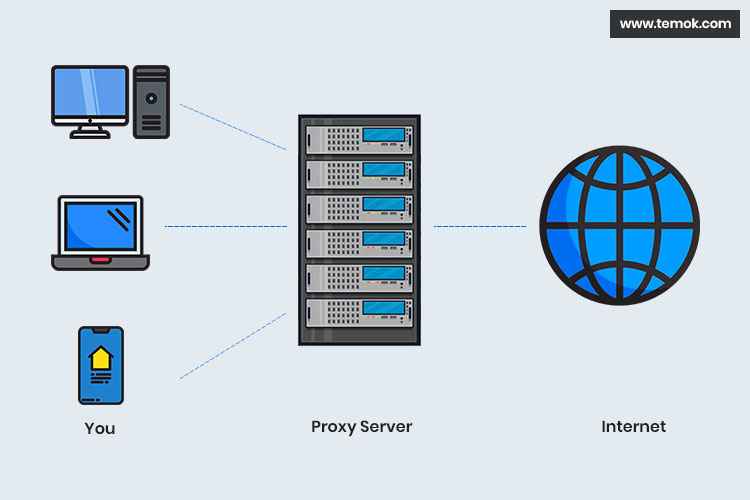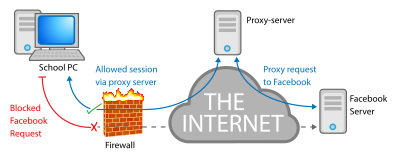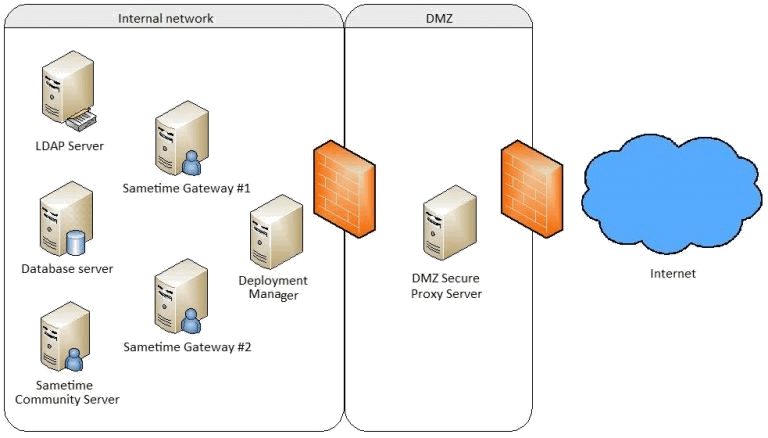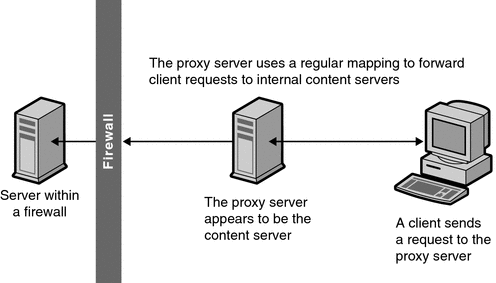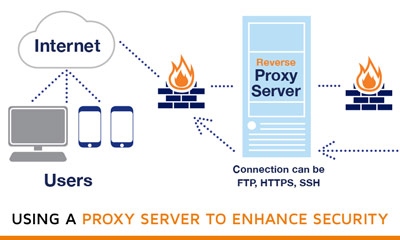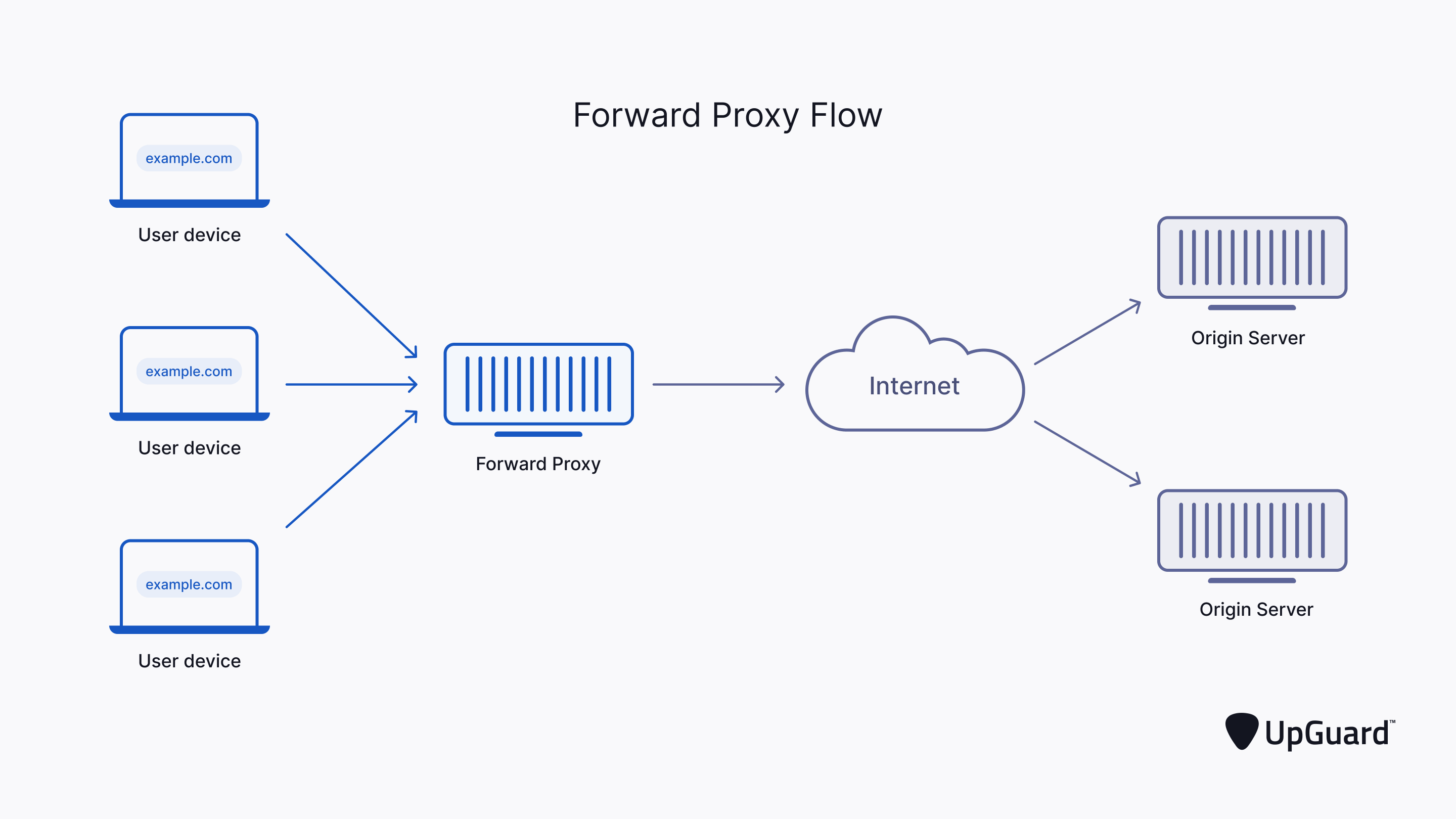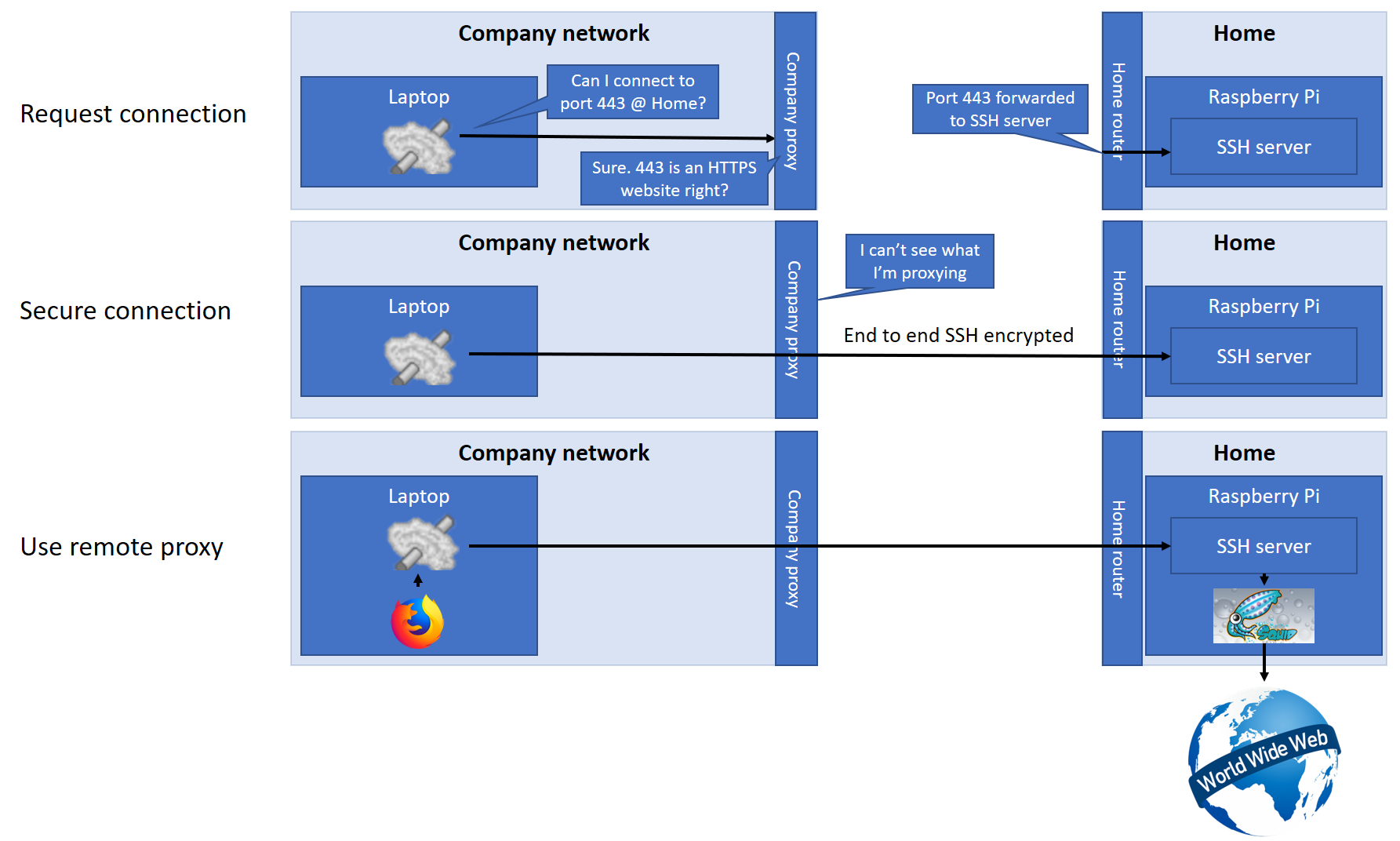
Security How to securely access remote content without using a VPN: Use a proxy server accessed through an SSH tunnel - AMIS, Data Driven Blog - Oracle & Microsoft Azure
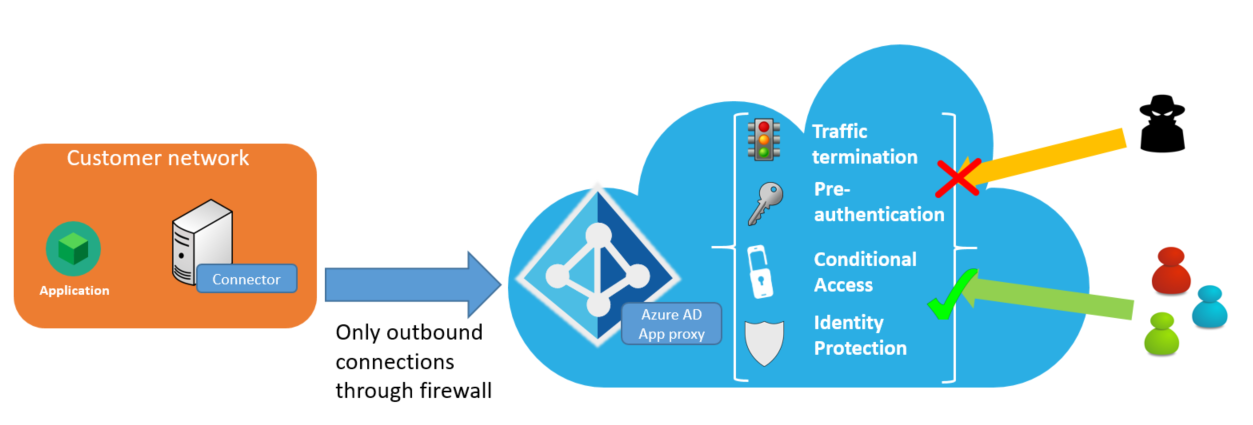
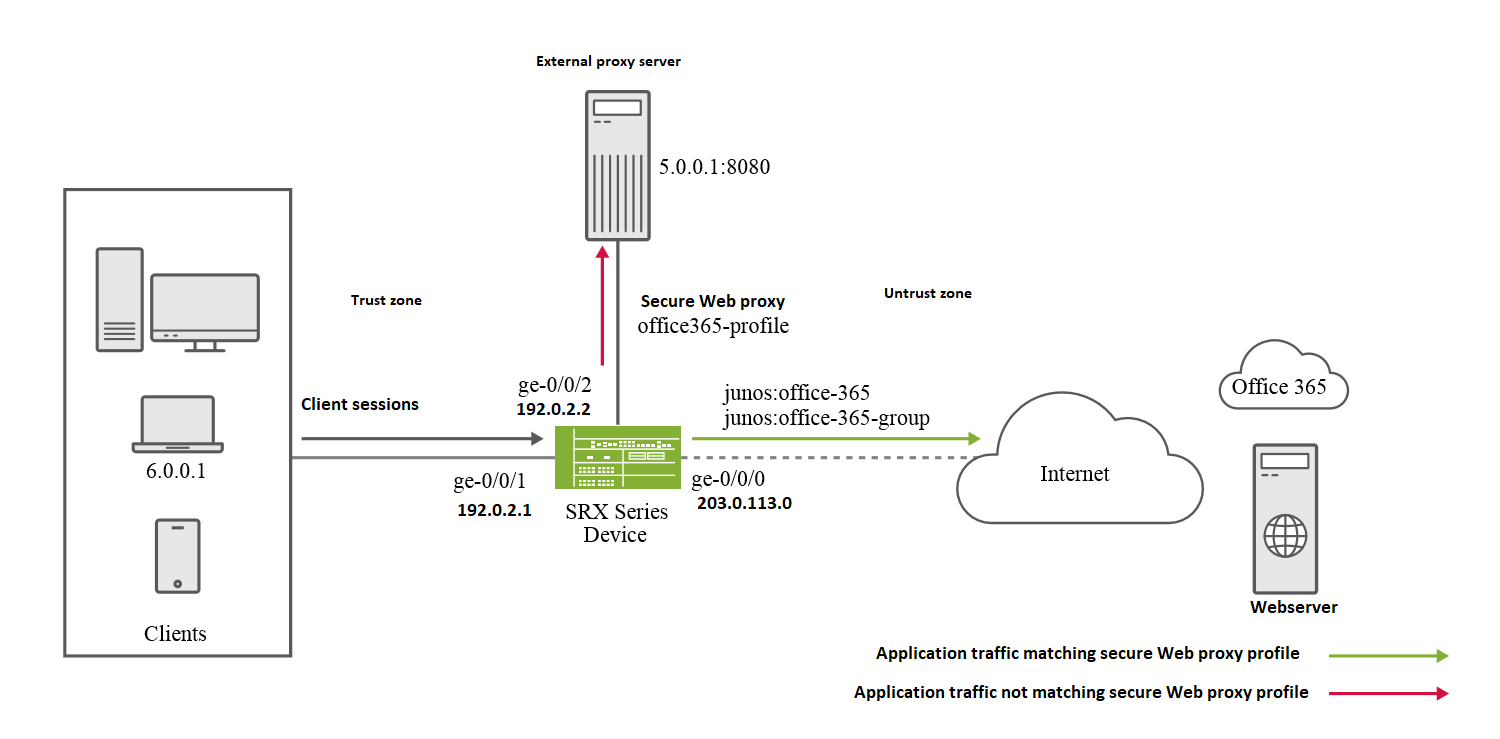
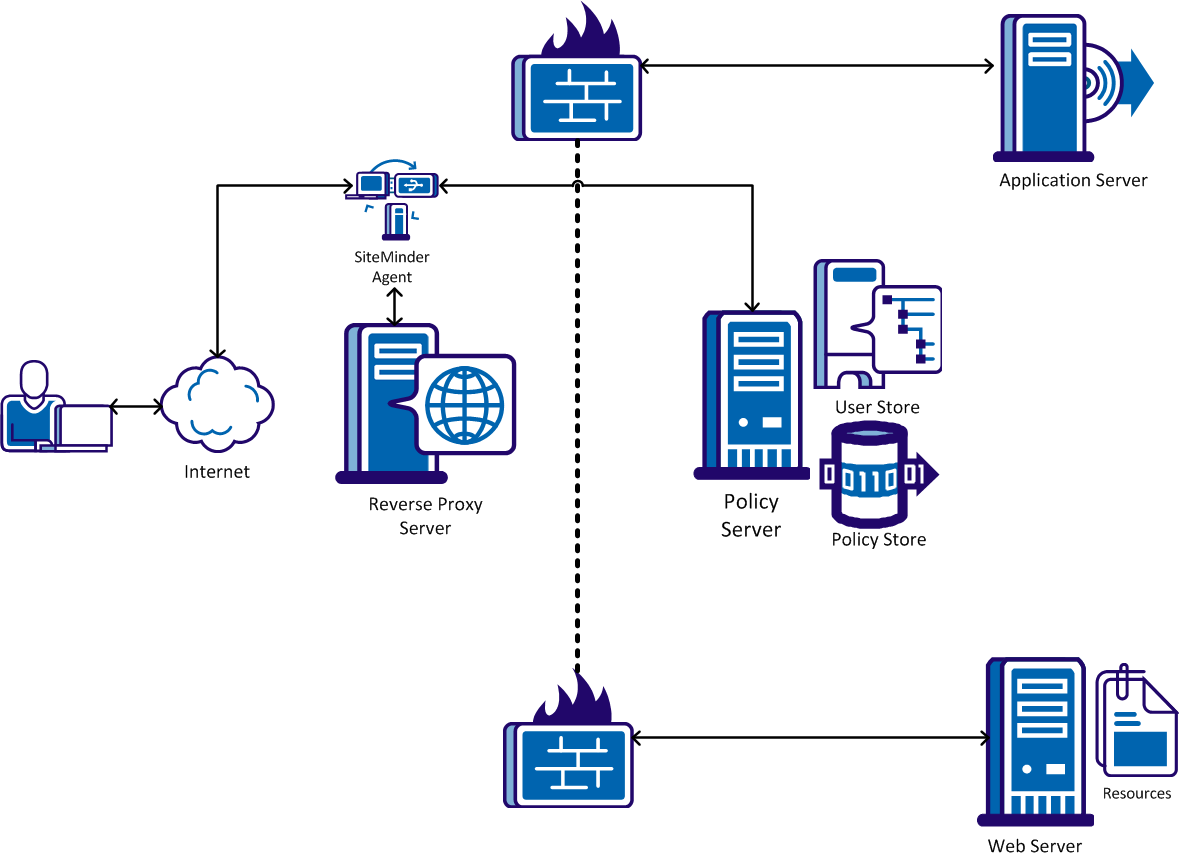
Security considerations for Azure Active Directory Application Proxy - Microsoft Entra | Microsoft Learn