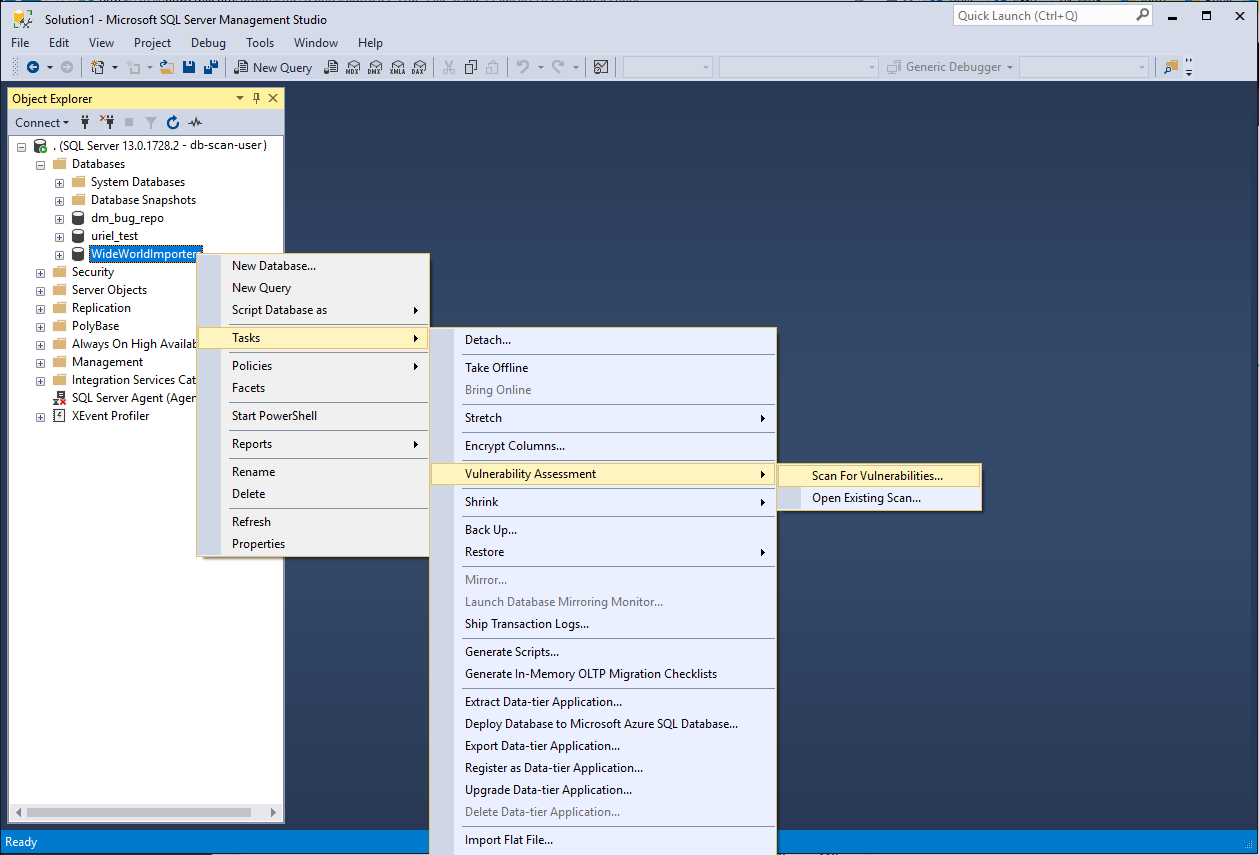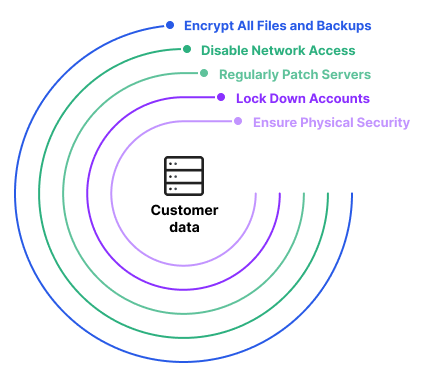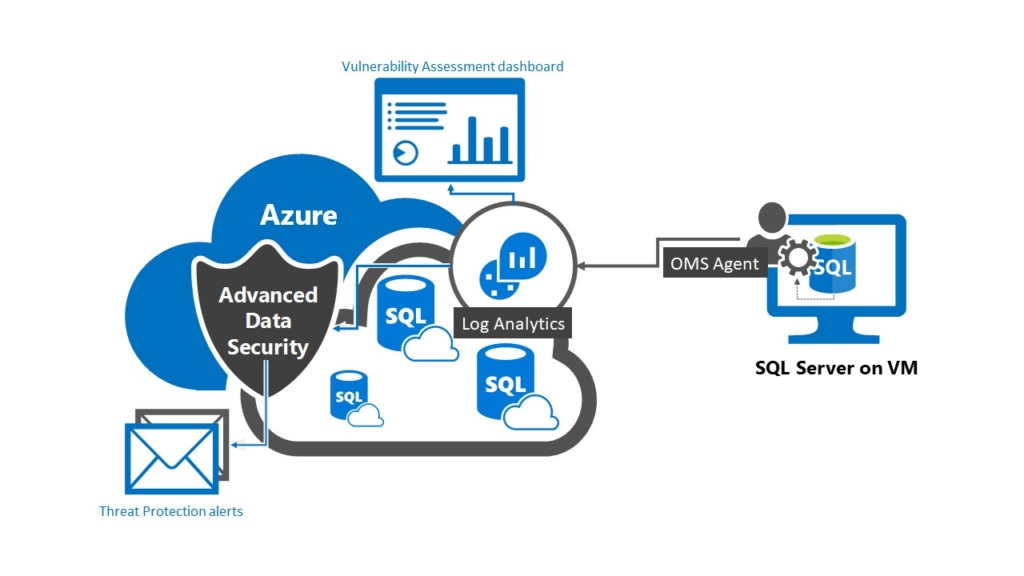
Advanced data security for SQL Server is coming to Azure Virtual Machines - Microsoft SQL Server Blog

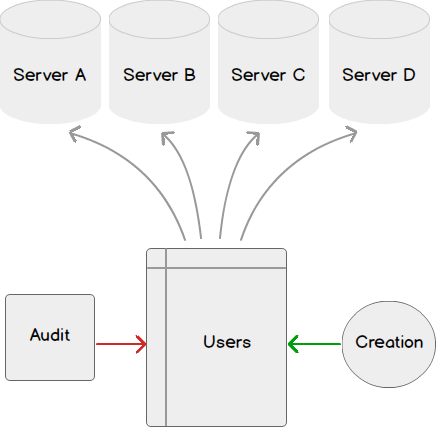
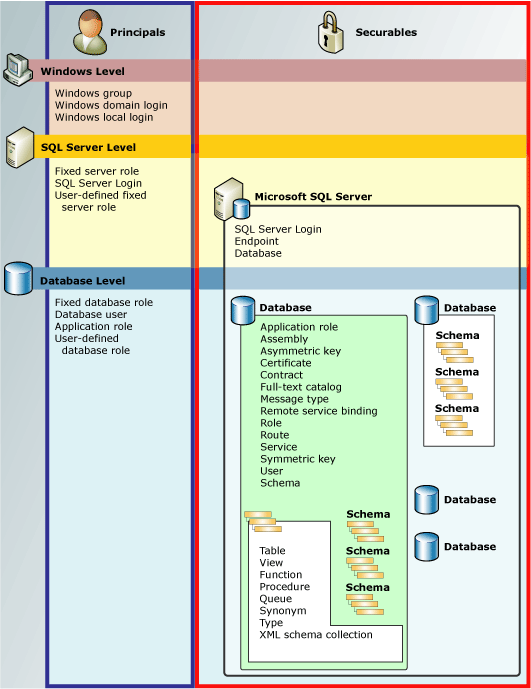
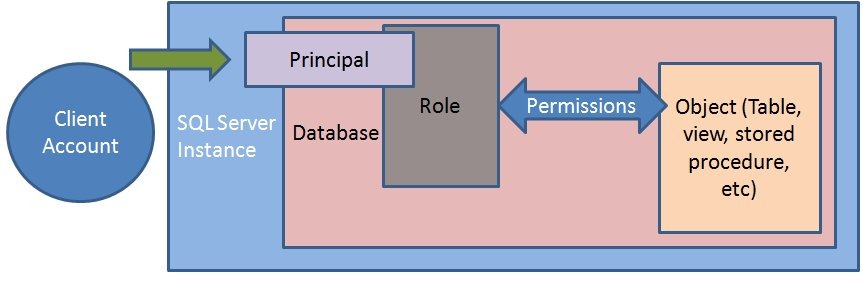
SQL Server 2019 Users and Security |SQL Server 2019: Security with Users, Schemas, and Roles - YouTube

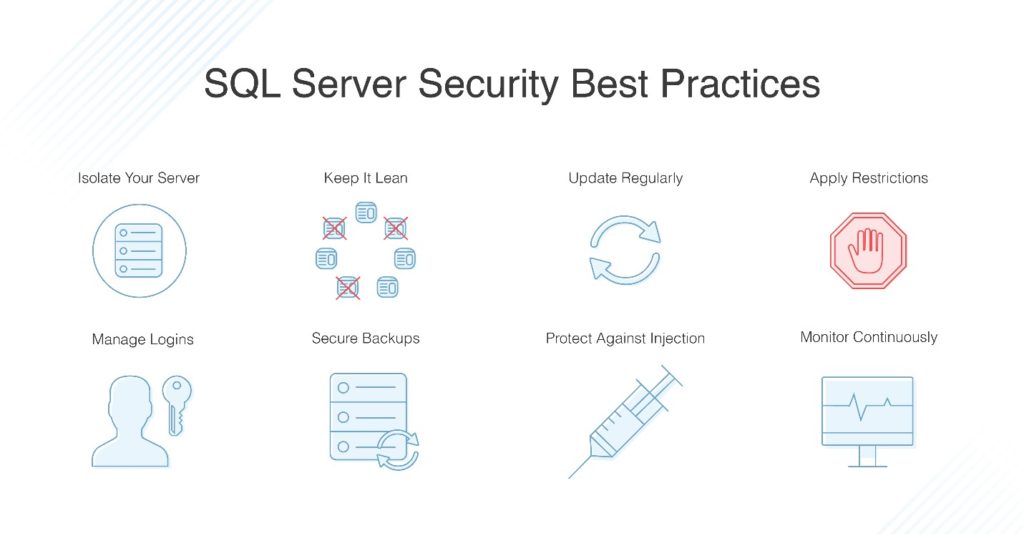
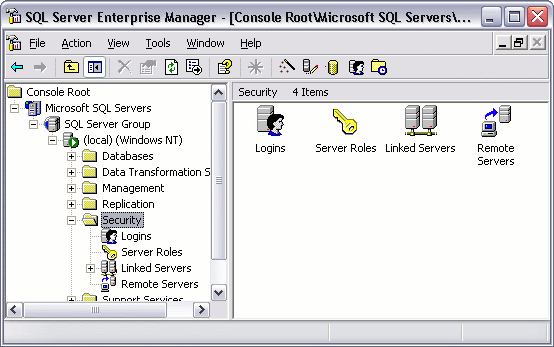
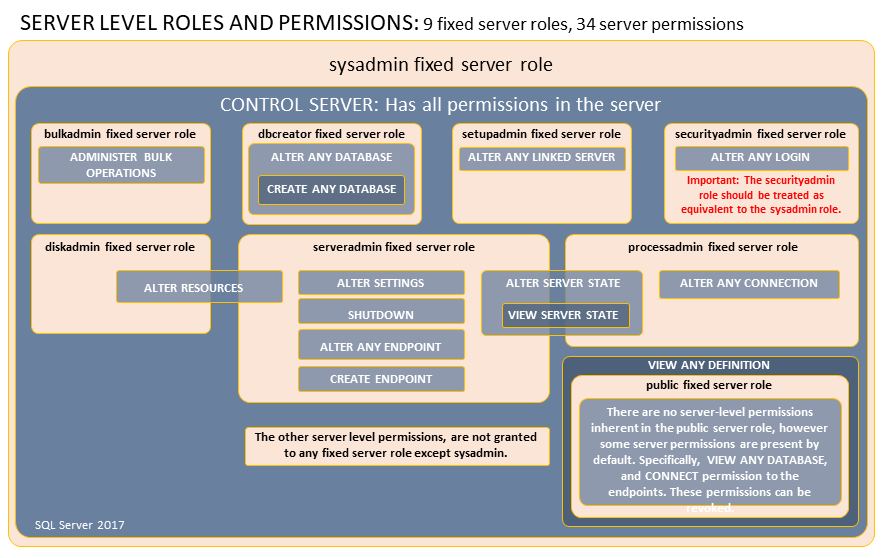
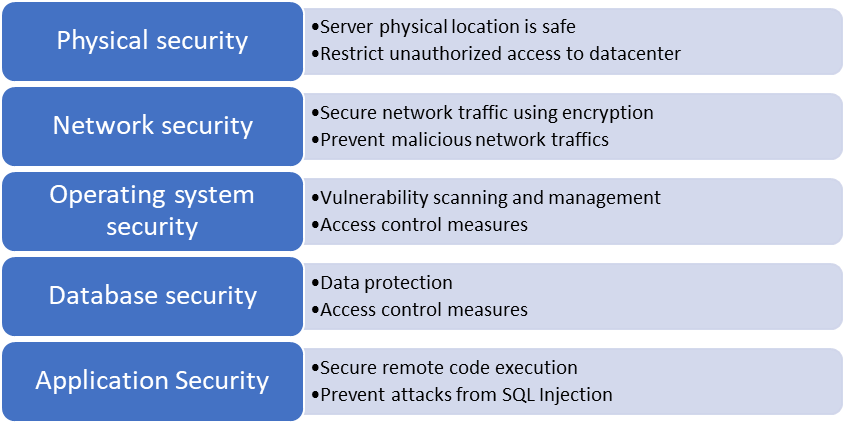
Securing Your SQL Server Environment | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More